Adding Trusted Sites to uBlock Origin via Group Policy
Background
At the company I work for, I rolled out uBlock Origin to all employees, a very popular browser extension designed to block advertisements and other unwanted content on websites. The main goal was to reduce the risk of malvertising, but it also helps make internet browsing more convenient. The implementation was straightforward using Group Policy, and the benefits were immediately apparent. However, an unexpected challenge quickly arose: a surge in help desk tickets indicating a couple internal websites were broken with uBlock Origin enabled, an issue that I had somehow missed during testing.
uBlock Origin offers a simple solution for handling broken websites: Trusted Sites. However, instructing hundreds of employees on how to trust the affected websites was far from ideal. I expected the flow of help desk tickets would continue as new employees joined and others forgot the instructions. While I would have preferred to fix the affected websites, they were developed and maintained by third parties, limiting my ability to make any changes.
Instead, I decided to explore using the same Group Policy Object (GPO) which installed the extension to also include a list of trusted websites. The process was surprisingly straightforward, though the available documentation I had to reference was somewhat sparse and confusing. This blog post serves to document and share the steps I took to use Group Policy to automatically trust specific sites in uBlock Origin, eliminating the need to send instructions to users or directly interact with endpoint systems.
This procedure was developed and tested on Windows Server 2022 domain controllers, with a mixture of Windows 10 and Windows 11 endpoints. The web browsers involved were Google Chrome version 126.0.6478.127 and Microsoft Edge version 126.0.2592.87, both using uBlock Origin version 1.58.0, which were the latest versions at the time of publication. Keep in mind that web browsers update frequently, which may cause some of the details presented here to become outdated over time.
Initial Configuration
To provide context, this is how I set up Group Policy to deploy uBlock Origin to Google Chrome and Microsoft Edge across the organization.
First, I downloaded the adminsitrative templates for both Google Chrome and Microsoft Edge. These templates are essential as they provide the policy definitions needed to easily manage the browsers through Group Policy. They can be downloaded from the following links:
- Google Chrome: https://chromeenterprise.google/download/
- Microsoft Edge: https://www.microsoft.com/en-us/edge/business/download
Once downloaded, I added these templates to the central store of the domain. Next, I created new GPOs for applying policies to the browsers. I used separate GPOs for Google Chrome and Microsoft Edge since they are different applications, but they can be combined into one if preferred.
The relevant policy settings for controlling extensions are located in the following folders:
- Google Chrome:
User Configuration -> Policies -> Administrative Templates -> Google -> Google Chrome -> Extensions - Microsoft Edge:
User Configuration -> Policies -> Administrative Templates -> Microsoft Edge -> Extensions
To deploy uBlock Origin, I configured the following policy settings within those folders:
-
Google Chrome
-
Policy Name:
Configure the list of force-installed apps and extensions- Value: Enabled
- Add to List:
cjpalhdlnbpafiamejdnhcphjbkeiagm
-
Policy Name:
-
Microsoft Edge
-
Policy Name:
Control which extensions are installed silently- Value: Enabled
- Add to List:
odfafepnkmbhccpbejgmiehpchacaeak
-
Policy Name:
The "Configure the list of force-installed apps and extensions" policy setting for Google Chrome forces the installation of uBlock Origin (extension ID: cjpalhdlnbpafiamejdnhcphjbkeiagm). Similarly, in Microsoft Edge, the "Control which extensions are installed silently" policy setting (except using extension ID: odfafepnkmbhccpbejgmiehpchacaeak) achieves the same goal. An extension's ID can be found in the URL of the extension's page on the Chrome Web Store or Microsoft Edge Add-ons site.
In the same folders, I configured two additional policy settings to block users from installing any extensions, with exceptions for the forced installation of uBlock Origin and the optional installation of certain extra extensions used by some, but not all, users. As an example in this post, I set up KeePassXC-Browser as an optionally available extension.
-
Google Chrome
-
Policy Name:
Configure extension blocklist- Value: Enabled
- Add to List:
*
-
Policy Name:
Configure extension allow list- Value: Enabled
- Add to List:
oboonakemofpalcgghocfoadofidjkkk
-
Policy Name:
-
Microsoft Edge
-
Policy Name:
Control which extensions cannot be installed- Value: Enabled
- Add to List:
*
-
Policy Name:
Allow specific extensions to be installed- Value: Enabled
- Add to List:
pdffhmdngciaglkoonimfcmckehcpafo
-
Policy Name:
For Google Chrome, the "Configure extension allow list" policy setting specifies which extensions may be installed by users, while the "Configure extension blocklist" policy setting designates which extensions are prohibited. Similarly, in Microsoft Edge, the "Allow specific extensions to be installed" policy setting allows certain extensions, and the "Control which extensions cannot be installed" policy setting blocks others. By adding an asterisk to the blocklist, it blocks all extensions, creating a deny-by-default, allow-by-exception policy. This setup ensures that only trusted extensions, like uBlock Origin and KeePassXC-Browser in this example, can be installed. While this restriction isn’t necessary to configure uBlock Origin, I highly recommend it for improved resistence to malicious extensions.
After making the described changes, this is what my GPOs looked like:
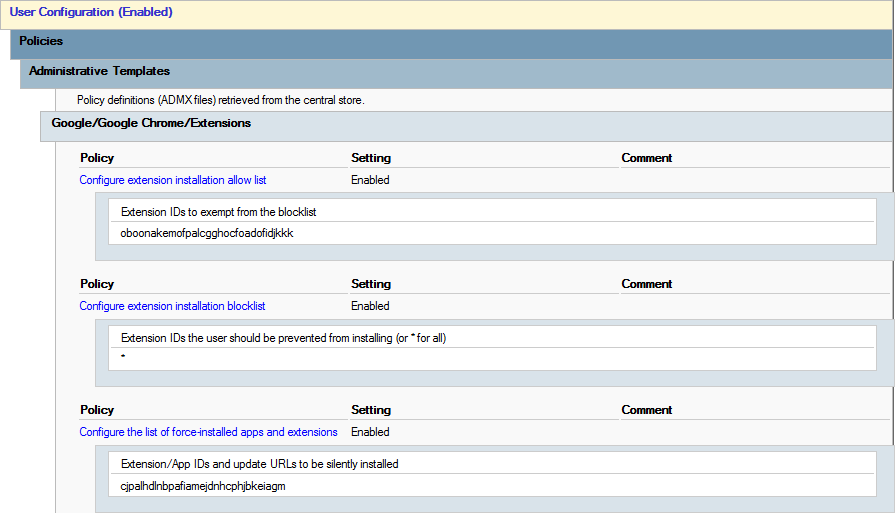
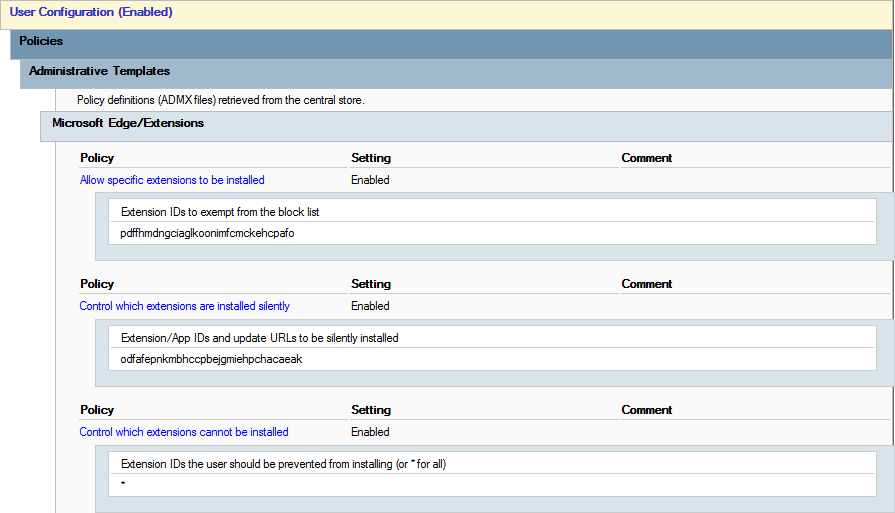
By this point, any user with the policy applied will have uBlock Origin forcefully installed, but will not yet have any trusted sites added by default.
Adding Trusted Sites
Now that uBlock Origin is deployed, the next step it to add trusted sites. To start, I created a simple JSON string based on the below template which contains the sites to be trusted. As an example, I included the public example domain and my personal domain.
{
"trustedSiteDirectives": [
"example.com",
"logal.dev"
]
}Next, I minified the JSON string to fit onto a single line. This can be done by hand, but it is a good idea to use a minifier tool to reduce the chance of creating a syntax error.
{"trustedSiteDirectives":["example.com","logal.dev"]}Returning to the previously created GPOs, I proceeded to add new registry items. These items are configured under User Configuration -> Preferences -> Windows Settings -> Registry. I created a new registry item in each GPO with the following values:
- Action:
Update - Hive:
HKEY_CURRENT_USER - Key Path:
- For Google Chrome:
Software\Policies\Google\Chrome\3rdparty\extensions\cjpalhdlnbpafiamejdnhcphjbkeiagm\policy - For Microsoft Edge:
Software\Policies\Microsoft\Edge\3rdparty\extensions\odfafepnkmbhccpbejgmiehpchacaeak\policy
- For Google Chrome:
- Value Name:
toAdd - Value type:
REG_SZ - Value data:
{"trustedSiteDirectives":["example.com","logal.dev"]}- This is the minified JSON example string from before.
- All remaining settings at default values.
These registry items configure an extension policy targeting uBlock Origin, specifically its "toAdd" property. The policy tells uBlock Origin to add the specified sites to the trusted sites directive. uBlock Origin offers several more properties that allow customizing nearly every aspect of the extension. However, my specific goal was to add trusted sites, and I also encountered some difficulty getting other properties to work during experimentation.
After incorporating the registry items, this is what my GPOs now looked like (the previously added policy settings are minimized):
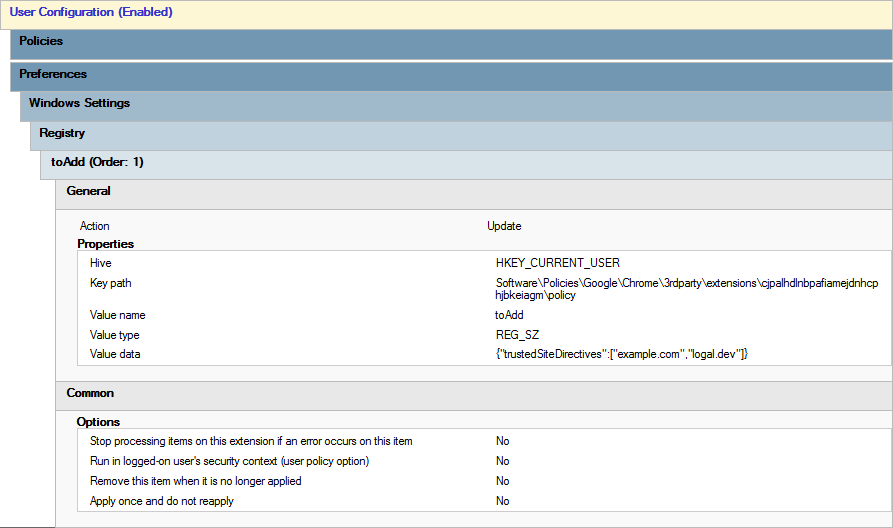
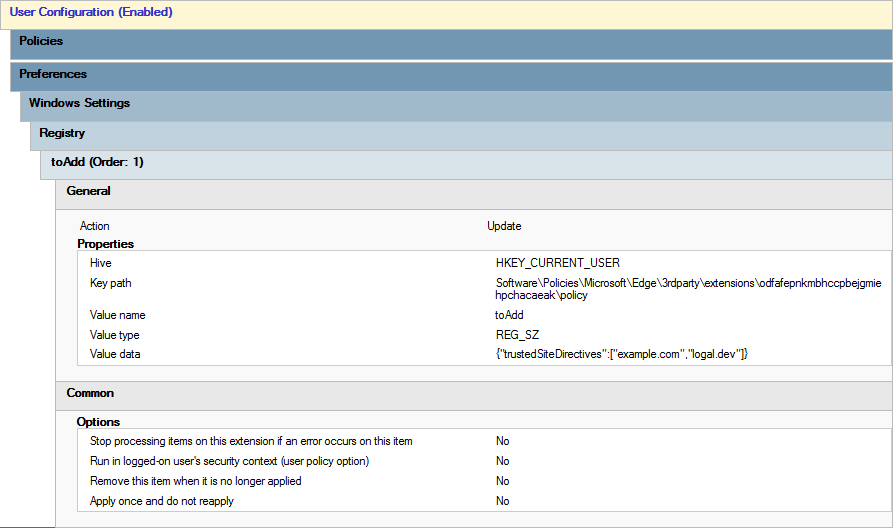
At this point, any user with the policy applied will have uBlock Origin forcefully installed with the specified domains added to the trusted sites list. This can be verified by checking the trusted sites tab in the uBlock Origin settings. The new domains should appear automatically without any manual intervention.
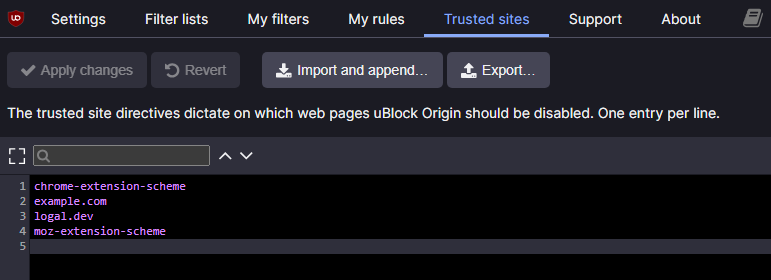
Based on my experience, the policy usually takes effect on the next browser startup. However, there are instances where the trusted sites list may not update immediately, especially if the browser was active during the Group Policy update. In the worst-case scenario, restarting the endpoint has always ensured the policy applied correctly.
Final Thoughts
It's worth noting the policy adds items to the trusted sites list rather than overriding it. This means users can still add their own trusted sites and the policy won't interfere. The only exception is if a user removes a site that the policy has trusted, it will be re-added as trusted on the next browser start.
It seems like adding trusted sites to uBlock Origin in Mozilla Firefox via Group Policy is possible, but not as straightforward as it is for Google Chrome or Microsoft Edge. Given Firefox's limited adoption within the company I work for, I didn't dive very deep into tailoring this procedure for it.
Looking ahead, the upcoming deprecation of Manifest v2 extensions in Google Chrome and Microsoft Edge could render this procedure obsolete in the near future. If the changes are implemented as expected, uBlock Origin will likely no longer function how it does in its current form. Luckily, a Manifest v3 variant called uBlock Origin Lite is already available for both browsers. Its README file mentions an administrative policy called noFiltering which might replicate the trusted sites functionality of uBlock Origin. I have not yet experimented with the specifics of configuring this policy using Group Policy, but I plan to revisit it closer to the Manifest v2 shutdown deadline date.
Any viewpoints expressed in this post are my own and do not reflect those of my employer or any other entity.